This is included in a multi-part series about the development of a digital resource addressing the Troubled Teen Industry (“TTI”) and introduces the concepts being applied regarding research and technical applications.
“A picture is worth a thousand words” evokes a sort of understanding rooted in sentimental to objective insight. Which is applied depends upon the viewer’s ability to deduce context and even lived experience seemingly unrelated. No longer limited to analog, digital images are more accessible and certainly worth more than just a thousand words. Of course this largely depends on how the viewer is able to effectively utilize the image both with insight and some strong technical skill.
Beyond just the context an image tells, a digital image possesses a story specific to being digital. Digital images contain information within its own file indicating when it was taken, what it was taken with, and possibly even exactly where it was taken. The “where” depends what took the photo such as a smart phone with GPS capabilities for example. Fortunately for the sake of security this information can be removed or stripped and some social media platforms do this automatically.
However digital images are only one part of the way research and information has become more accessible. The above addresses just one of the methods found within the use of OSINT or Open Source Intelligence.
What is OSINT?
OSINT is the gathering or collection of publicly available data which can become usable intelligence by the meaning it is given to answer specific questions. Without context to “why” and what purpose it serves it remains just raw data. Specific methods of analysis and exploration are required in order for raw data to be actionable intelligence.
A simple Google search or a list of links (possibly in the form of a “data dump”) is not OSINT as it does not make clear why the data matters. Moreover no real investigative process, exploration, or analysis has been applied to the data to extract its relevant value.
For this reason OSINT is more than just data collection but rather how we go about answering specific questions or facilitating an investigation. Now to achieve accurate and actionable intelligence the data collected is held to strict standards regarding its quality and authenticity. It isn’t just about how much is gathered but rather the usable intel gleaned to produce and disseminate.
As a researcher with a strong technical background interested in not only creating awareness but facilitating the ability for informed decisions to even be possible. In regards to both youth rights and addressing the industry offering treatment for “at-risk” or troubled youth, OSINT has been at the backbone of making that possible.
The Importance of OSINT
TRANSPARENT INVESTIGATION DEFINED
The authenticity and reliability of the information gathered is easily verified due to the transparency of the process. This process starts by defining the matter being researched and investigated and the reasons for doing so. Arguably the most significant is in achieving the desired end result which provides answers to inquiries posed about the subject being explored.
Most investigative processes follow a fairly similar protocol due to the requirements of fulfilling OSINT analysis. This is in order to produce usable and actionable intelligence so establishing the context of the research is involved during the investigation itself. By understanding how the process occurs it can be easily duplicated and verified as the data sources are openly accessible in nature.
Through using OSINT and its utility users can benefit from findings and apply this to their own decision making processes. OSINT breaks down the subject being researched along with the techniques best facilitate providing much needed information. A “just trust me” response is no longer required due to easily showing the work that’s been done.
DECISION MAKING: INFORMED CONSENT
For its most practical application OSINT shines as a viable option in fostering the ability to come to informed decision making. When using openly accessible sources along with the tools for comprehensive and thorough exploration much needed information can be attained. While this article serves simply as an introduction and overview various elements, this helps identify its value.
With more information available the ability to think critically is truly a sort of survival skill. While coming to conclusions has room for innovation, testing its reliability requires a deeper understanding of OSINT methods and applications. However, to be able to follow an established practice remaining open to both continual improvement and utilized for issues of a broader scope ultimately determines its potential.
When we make a choice we are consenting to a proposed solution. If that choice is made utilizing data that is either incomplete, inaccurate, or even deceptive then consent is unable to occur. The outcome is not as intended even bringing harm or significant risk in matters pertaining to our future and well being.
Practices within OSINT
METHODS AND TECHNIQUES
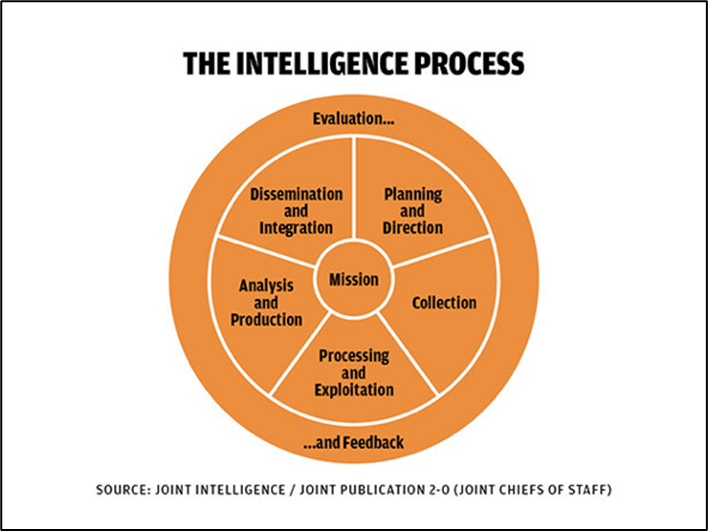
The primary structure associated with practicing OSINT effectively is known as an Intelligence Cycle and is not too dissimilar to other forms of scientific inquiry. Of course there are multiple approaches to this that are flexible towards the type of research being conducted. Even within this process is being able to determine, almost as importantly as usable information, how to best obtain that information so that a specific, reliable approach is identified.
The tools such as software, applications, and other resources are often created as a result of discovering effective measures during the intelligence cycle of an investigation. Having practices in place for exploring and discovering both raw data and findings within that raw data acts to continually improve further research conducted.
Data Scraping & Archiving Web scraping involves using software tools to extract data from websites gathering large amounts of data quickly and efficiently. This can even be automated as technology advances both expediting retrieval and cross referencing multiple findings and data points.
Data Analysis Includes the specific tools used to identify patterns and relationships as well as the insight or approach towards exploring data collected. Such examples can range from the use of Excel spreadsheets to more complex implementation of different database infrastructures. Entering and processing data can be complicated even for the more experienced user. Understandably such a career remains highly sought after due to continual demand and attractive salary.
Ideally they function to allow for unique exploration to produce statistics or measurable findings which decision making is based upon. From the use of a cycle this is continuous and able to be improved upon over time adapting to not only discovered intelligence but the technology that continues making it possible.
AI & Language Learning Models better known presently as OpenAI or ChatGPT are not as innovative as one may think or dooming humankind to an inevitable dystopian future. A topic to be further explored in the future, technology is only as evil as the person who operates it. Now that may not add too much of a sense of comfort but this kind of technology is of significant benefit to efficient dissemination of information.
With the anticipation of a project a long time in the making, examples of these methods and how they function pertaining to an current issue affecting youth will be explored. The support of that work along with NYRA is what makes it possible to continue developing as a valuable resource.




Examples of various Intelligence Cycles for different use cases
SOURCES USED IN COLLECTION AND RESEARCH
Public Records Usually by request this includes court documents, property records, and business filings. This provide insight on individuals, organizations, and other entities.
News & Social Media Platforms like X (formerly known as “Twitter”), Reddit, Facebook, LinkedIn, and so on are valuable OSINT for individuals. Sources such as newspapers, magazines, and online outlets can monitor and analyze current events and potential threats. Such sources must be cross referenced and verified but serve as establishing relevant key data points.
Digital Media (Images, Videos) As mentioned previously, digital images and other multimedia provide more than what is at surface level.
Academic Libraries & Datasets Although some of the most in-depth available data for investigations it can come at a literal price limiting accessibility. Research and academic studies can often be behind paywalls or accessible to students enrolled in university. Government websites may provide extensive datasets of various departments regarding oversight on spending and performance.
Dark web (Tor) websites, databases, files, and more that cannot be indexed by traditional search engines. Most deep web content is public although with an intimidating learning curve.
These examples are certainly not exhaustive. Ultimately OSINT remains within what is not only legally viable but usable as evidence within court cases and proceedings.
Ethical Concerns: User & Data Privacy
OSINT itself is valuable but it can be misused for malicious purposes in the same way information can be weaponized. This can fall under cyber-stalking, harassment, or doxxing and is crucial to be aware of such risks. Concerns regarding user privacy are especially important when incorporating OSINT into research where Personally Identifying Information (“PII”) can be exploited. The incorporation of a defined set of best practices to address potential risks is ultimately an absolute requirement.
In leading up to presenting the work being developed with NYRA along with support from aligned organizations additional articles will be available continuing education on this subject. OSINT, appearing less common in the U.S., has established an online community of professionals and enthusiasts passionate on the subject. We will continue to address this approach and how it has been effectively utilized including the UC Berkeley School of Law Protocol for OSINT Investigations publication and the progress OSINT has facilitated.
REFERENCES USED
- https://www.sans.org/blog/what-is-open-source-intelligence/
- https://bellingcat.com
- https://medium.com/@mohitdeswal_35470/the-beginners-guide-to-open-source-intelligence-osint-techniques-and-tools-6a91b9c37ee1
- https://www.recordedfuture.com/open-source-intelligence-definition
- https://cltc.berkeley.edu/about-us/citizen-clinic/citizen-clinic-cybersecurity-education-center/open-source-research-methods-safety-and-tools/
- https://books.google.com/books?id=pCOFOqD9TYQC&lpg=PA75&ots=FIhMGhTTre&dq=OSINT%20for%20research&lr&pg=PA83#v=onepage&q=OSINT%20for%20research&f=false
- https://ieeexplore.ieee.org/abstract/document/8954668
- https://drive.proton.me/urls/AYVTGCDKXR#ugBGvS4f7aU4






In Florida, as in many other States, the voter list is unrestricted, public information. Moreover, as each monthly edition issues, more information becomes public. The list provides a unique voter ID number, the birthdate, sex, name and address among other data. It took a while but the pre-registered persons younger than 18 years are excluded now. Even so, If the voter lived with parents at 123 Sesame Street, Apartment 456 at age 18, that fact does not disappear from history when a new list issues; it remains part of the old lists that some persons retained.
Let’s say you’re going on a date with Caitlyn, and you click a few keys and learn that Caitlyn is listed as female on the voter list, but Caitlyn’s voter ID number used to belong to somebody named Bruce, listed as male, on a previous voter list. You click a few more keys and learn that Bruce won Olympic medals in the men’s division. One school of thought holds that when you go on a date, lovey dovey, kissy kissy, you aren’t supposed to care if your date is a man or a woman. Another school of thought holds, as the song goes, you must be sure that the girl is pure with that Funky Cold Medina.